Multi-factor Authentication (MFA) is one of the smartest security practices to roll out at your organization to prevent a data breach. But it isn’t bullet-proof. Deploying multiple Microsoft Azure 365 identity and access management security measures can help maximize protection of your tenant.
Eric Raff, Cloud Practice Director at JourneyTeam in a presentation hosted by buckleyPLANET to the Utah SharePoint User Group (UTSPUG) and Microsoft User Group (MUGUT) shared the top 10 security tips and considerations after you’ve rolled out MFA in your Microsoft Dynamics 365 tenant. Raff is a 25+ year expert in Identity and Access Management in Microsoft 365 and Windows Azure.
To recap, Part 1 covered the following security best practices:
- Check Your Security Defaults
- Block Legacy Protocols
- Set Restrictions on Guest Access
- Manage Consent and Permissions for Enterprise Apps
- Must-have Azure Portal Settings
To learn more about these tips, including a step-by-step guide for how to implement each best practice, check out Part 1!

Now onto the second half (tips 6-10) of the Raff’s security best practices to deploy along with MFA.
6. Set up Access Reviews
Periodically performing Azure AD access reviews is a smart practice. Using the Access Review feature requires an Azure AD P2 license. Access Reviews allow you to set up reviews for group membership and application assignments.
Access Reviews for Azure AD Enterprise Apps is discussed in number 5 (in Part 1), and review of Azure AD roles are completed in Privileged Identity Management (PIM) as discussed next in number 7.
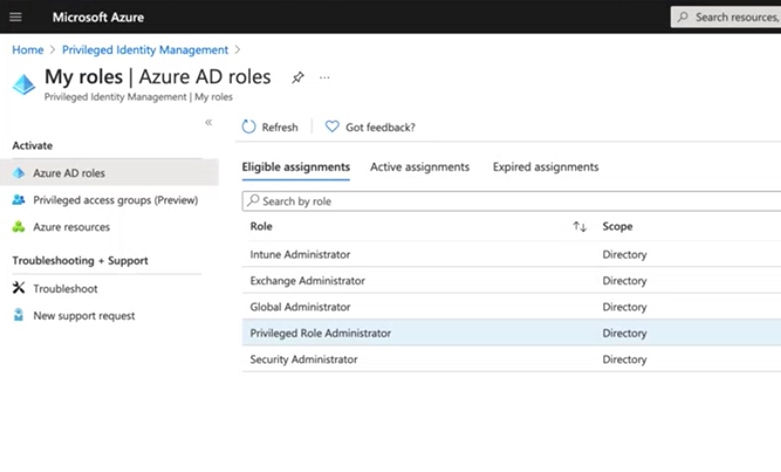
7. Review Roles in PIM Privileged Identity Management (PIM) is an Azure AD service used to manage your resources, including showing you who has what roles in your organization.
- In PIM, go to “Azure AD Roles”
- Here you’ll see the grand list of all of the users in the tenant, along with their roles. If you’re ever asked to produce a list including names, roles, emails and how they got their role, you can export a report to CSV format.
In cases where you need to take on a temporary administrator role to complete a specific task, you can set this up in PIM also.
- In the Azure portal, go to “Active Directory.”
- Here you can view your current role. Go to “Privileged Identity Management” > “My Roles” to see what roles you are eligible for and can activate. You can request certain Administrator roles for up to 10 hours.
- Under “Active Assignments,” you can view your temporary role and deactivate once complete.

8. Set up MCAS Policy to Enable Real-time Monitoring As a follow up to number 4 in Part 1 and an added layer of security, you can use a Microsoft Cloud App Security (CAS) and OAuth policy to control access to cloud apps. Access control can be based on the user, location, device and apps. To leverage CAS to alert and revoke access to uncommon or rare apps asking for high levels of permissions, you can create a filter for the policy.
- To create a policy, go to the Cloud App Security Portal at portal.cloudappsecurity.com or through the Microsoft 365 Admin Center, then “Control” > “Policies” > “Conditional Access.”
- Here you can create a policy for apps in which the permission levels are very high, and the community use is not common. The policy can create an alert, as well as revoke access to the app.
9. Conditional Access Policy for Admin Roles Admin Roles are often prime targets for attacks. In addition to MFA, Conditional Access (CA) policies can provide extra protection. Here is how to create a new CA policy for Admin Roles, and the suggested parameters:
- From Azure Portal go to “Security.”
- Go to “Conditional Access Policies” > “New Policy.”
- Type in a name such as “Require MFA and Compliant Devices for Admin Roles.”
- “Select Users and Group” and select the specific roles that you want in this group.
- Go to “Cloud Apps or Actions” and select “All Cloud Apps.”
- Go to “Conditions” and select whatever is applicable.
- Go to “Access Controls” and select “Require Multi Factor Authentication” as well as “Require Device to be marked as compliant” and “For multiple controls, require all the selected controls.”
10. Save your Log Files To ensure you have the data you need for future reference at any time, it is important to keep track of sign-ins, changes to the tenant, and tracking of who did what (and when). There is a native integration between Azure AD and Azure Log Analytics (Azure Monitor) that provides an easy way to save and export your log files for review:
- When you look at sign-in logs, if you only see 7 days or 24 hours as date options (and not 1 month), this means you do not have Azure AD premium in your tenant. It is advised that you have at least one license of Azure AD premium to get monthly logs (as well as other benefits).
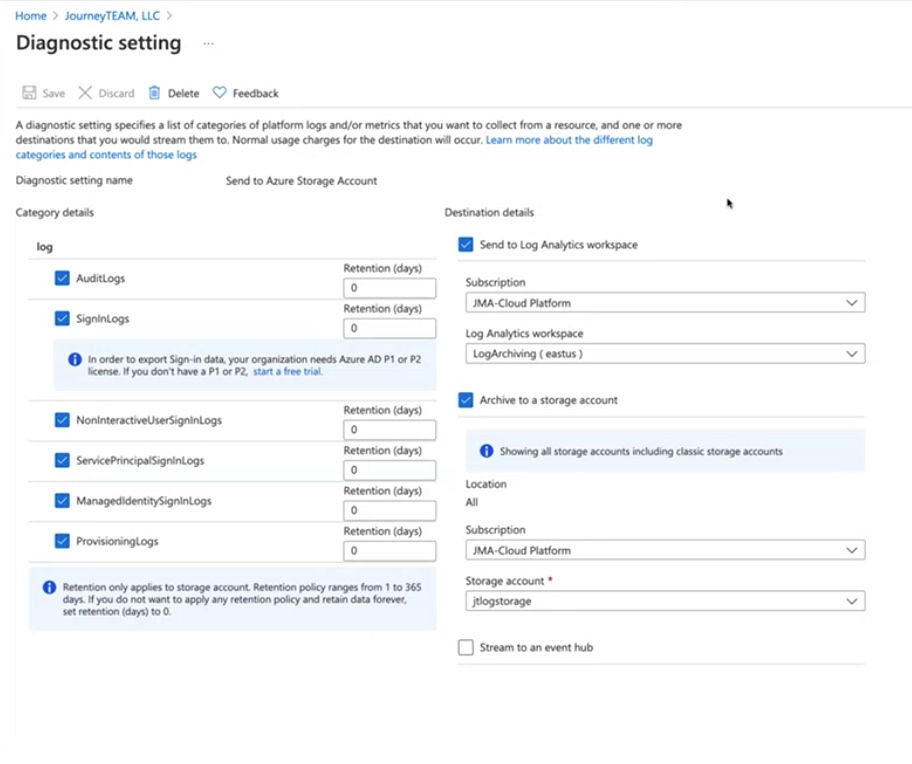
- To export logs longer than one month in the Azure AD Portal, go to “Monitoring” > “Logs” > “Diagnostic Settings.”
- Here you can edit your settings to configure the export of your logs including its destination.
- Click “+ Add Diagnostic Setting” to create an Azure Log Analytics workspace.
- Click “Edit settings” to select the destinations to stream to or archive, as well as select categories of platform logs and metrics (and indicating the length of retention, 1 – 365 days):
- “AuditLogs”
- “SigninLogs”
- “NotInteractiveUserSigninLogs”
- “ServicePrincipalSigninLogs”
- “ManagedIdentifySigninLogs”
- “ProvisioningLogs”
- Then send to the right Azure subscription to the Log Archiving Workspace. You can also send them to a storage account.
This concludes the top 10 security tips to deploy in your tenant after enabling MFA!
Microsoft 365 | Azure | Cloud | Office 365
For any additional questions, please contact Journeyteam at (801) 565-9199


